
In an age when technology changes at a rate faster than ever before, new means of communication, collaboration and data storage have brought in unprecedented rise in productivity and lowered costs beyond imagination. On the flip side, however, modern threats to security of IT systems, applications and data have also evolved as rapidly as their legitimate cousins, giving rise to a global security industry worth billions of dollars. All the research and vigilance, however, can one day turn to naught, and eternal vigilance has become the price one must pay for securing cyber assets –tangible and intangible
In the 1950s, a blind American kid Joe Engressia discovered that a certain whistling tune could stop recorded phone messages. Soon, others had discovered tones and pitches that enabled them to make free phone calls. In the 1980s, hackers like Kevin Mitnik gained worldwide prominence. At the time of his arrest in 1995, Mitnick was on the US’ most wanted list and had to spend a year of his sentence in solitary confinement because the judge was told he could whistle the nuclear launch codes into a phone, prompting the judge to order that Mitnik would not be allowed to even touch a phone or modem! The only way of doing this was by putting him in solitary, and he thus spent an entire year alone in a cell.
The world has moved a long distance from the days of Engressia and Mitnick. As computerised information systems become almost ubiquitous and assume control of critical services and infrastructure, threats to security are much more serious than ever before. Similarly, financial data is almost exclusively maintained in electronic form, and any unauthorised access to such applications and data could wreak havoc. In an increasingly integrated world, the consequences of any such mishap might not remain confined to a single economy.

Emerging Threats to Security
Security of infrastructure, data and applications is an increasingly complex, 24X7 job. One has to practically keep running to stay in the same place. One slip-up is all it takes for valuable, confidential business data to be compromised – leaving in its wake not only financial loss, but also loss of trust – something far more difficult to recoup than money. In an increasingly interconnected world, news travels fast, and bad news travels faster. Security for IT is no longer an option, it is a core part of any solution implementation.


Lucius Lobo
Vice President and Global Head, Security Services, Tech Mahindra
“Social engineering attacks on employees to obtain confidential information will be the biggest threat in 2012”
Talking of the biggest emerging threats to IT security in the current scenario, Lucius Lobo, Vice President and Global Head, Security Services, Tech Mahindra, says social engineering attacks on employees to obtain confidential information will be the biggest threat in 2012. Lobo fears employees could become victims of such attacks through malware or by phishing. RSA’s Country Manager for India and the SAARC Region, Kartik Shahani says new forms of exploits such as Man in the Browser (MITB) attacks would become more frequent. MITB attacks are designed to infect a web browser with malware that can result in modified web pages and transactions that are largely transparent to both the user and the host application. Such attacks can lead to illegal money transfers, identity theft, or the compromise of valuable enterprise information. Shahani also says that securityrelated information, and not financial data is now the major object of desire for hackers. Echoing Lobo, eScan CEO and MD Govind Rammurthy also picks social engineering as the standout threat. Shahani identifies a class of threats known as Advanced Persistent Threats (APTs), which combine social engineering techniques with other technical means to gain illegitimate access to systems and information.
|
Stuxnet – first Cyberweapon? Stuxnet – a sophisticated worm that specifically targets Siemens-built systems – is believed to have been unleashed upon key Iranian nuclear installations in 2009-10. Stuxnet targets the Simatic WinCC Step7 software developed by Siemens. The software is deployed in industrial control systems and is used to program controllers that drive componentssuch as motors, valves and switches in a large number of industrial assemblies. It infects Windows systems and spreads via USB sticks, allowing it to infect ‘air-gapped’ systems – systems that are not connected to a public network such as the Internet. Stuxnet had four ‘zero-day exploits’ – vulnerabilities that were unknown and unpatched when the worm was released – in its repertoire, showing the technical sophistication that must have gone into creating the worm. Security researchers studying the exploit later discovered that computers in Iran formed the majority of compromised systems – a rarity in a world where the US is on the top of any malware infections. Iran later acknowledged that computers at its Bushehr plants had been infected. Iran’s largest plant at Natanz was also facing severe problems at around the same time. There is no conclusive way to establish whether Stuxnet was developed to target Iranian nuclear installations and unleashed upon them by another country, but the coincidences involved are too stark to be ignored. For now, the only thing that can be said with certainty is that Stuxnet takes us into a frightening new era where things such as water, gas and electric supply, things that we take for granted, might one day become weapons that can be turned upon us. |
Many of today’s malware could give professionally-written ‘good’ software a run for its money in design and sophistication. Take Stuxnet (see box) for example. A malware of such sophistication was never seen before. Stuxnet comes up in a conversation with Dr Gulshan Rai, Director General of CERT-In (Indian Computer Emergency Response Team) – India’s central authority for responding to security incidents in the cyber domain. Agreeing that Stuxnet was probably the outcome of a dedicated project, Rai says it showed the kind of dangerous weapons that can be fashioned through IT, and emphasises upon the need to incorporate such concerns into upcoming infrastructure. ESET India Director Pankaj Jain also brings up Stuxnet and social engineering.
New-age Technologies bring New-age Threats
With the huge savings, ease of access, consistency of data and information and other such attributes that it offers, the Cloud is fast becoming a favourite of the private sector as well as governments. A number of governments in India are now talking of moving to private clouds, and some pioneer states have already started the preliminary work in this direction. Similarly, the increasing ubiquity of mobiles – smart and dumb – have seen a boom in m-commerce and governments are now looking at m-Governance as the next step in e-Governance. This is not without threats, however. Both the Cloud and mobile platforms face a number of security issues that stand in the way of full-scale adoption.
The convenience and collaborative potential offered by the Cloud and mobile devices is a mixed blessing. While on the one hand it has opened up hitherto unimagined vistas and expanded business potential (for enterprises as well as governments), it has also ushered in a highly complex security environment where the conventional defences offered by security software and intrusion detection systems is proving to be virtually futile. RSA’s Shahani says that in this new era, conventional notions of security would have to change and become more agile and intelligence-based. Response times have to be brought down and vulnerability windows have to be shrunk. Security should be automatic and incident response needs to shift to real-time reporting and mitigation.

Kartik Shahani
Country Manager for India and the SAARC Region, RSA
“There’s still considerable confusion about how best to handle information security in the cloud”
Saying that existing and legacy government systems need to be upgraded on a priority basis in order to stand against modern threats, Tech Mahindra’s Lobo emphasises upon the need for a cultural change to enhance cyber security awareness among its employees, a point that CERT-In’s Rai concedes, saying that while the policy and legal framework relating to security has been considerably tightened, training and full adoption will take some time. Rai also points out the continuous efforts being made in this direction through regular security workshops and security drills being conducted by CERT-In, in partnership with industry groups, security agencies and the law and order machinery etc.
Talking of issues related to security of Cloud-based data and applications, as well as mobile platforms, Amit Nath, Country Manager, Trend Micro says the anywhere, anytime access made possible by such technologies is a security nightmare.
Ensuring Security
From the government side, the IT Act 2000 and its 2008 amendment form the bedrock of IT-related policies in India. Section 43A of the IT Act, introduced by the 2008 amendment, is primarily concerned with enhancing provisions related to data security and data protec- tion. However, this is mainly related to data security by corporations and fixes liabilities in cases of compromise of data. Dr Kamlesh Bajaj, CEO, DSCI (Data Security Council of India) – a specialised body set up by NASSCOM – outlines the steps his organisation has taken to promote data safety and security. DSCI has developed a set of best practices and frameworks in data security & privacy and is actively involved in promoting their implementation in the industry and government. In addition, it also conducts regular conferences and seminars etc., conducts trainings in cyber forensics and cyber crime investigations for law enforcement agencies; provides policy inputs to the Government and is also engaged in international collaborations. The DSCI Cyber Labs programme for training law enforcement officers would soon be upgraded to a national programme supported by Ministry of Home Affairs, Bajaj informs.
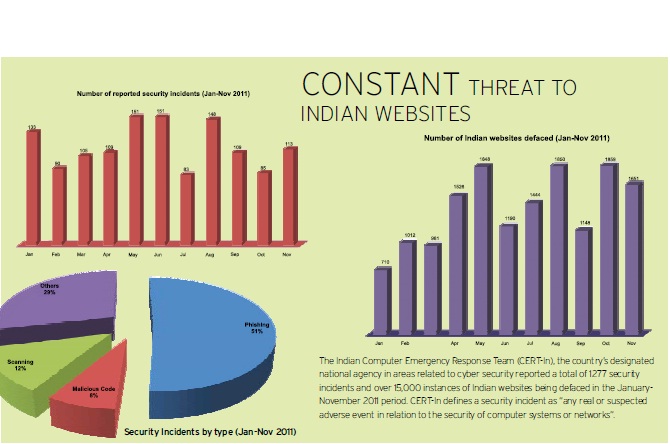
CERT-In is also actively engaged in helping improve the security stance of Indian websites, Rai discloses. CERT-In brings out regular bulletins and white papers on security threats, conducts trainings and workshops, security drills and audits to evaluate the preparedness of websites. In addition, it also helps compromised sites to get back on feet, all the while maintaining secrecy regarding its identity.

Pankaj Jain
Director, ESET India
“The number of threats for smartphones and tablets is growing rapidly, for all the platforms”
Shahani ticks off a set of key steps needed to ensure data safety. Key among these are: a stricter initial registration and validation processes; enhanced fraud monitoring; monitoring of the full network with cyber-forensic tools; strong authentication and access controls and encryption of data being transmitted etc. Bajaj emphasises the role of a security-oriented mindset, ongoing education & awareness on information security and privacy among individuals – employees, intermediaries and end-users.
Evolving Security Solutions
Kutty Nair, Chairman & Managing Director of Mielesecurity, says that modern antivirus consistently fails at protecting against anything other than consumer level or mass threats, and Lobo acknowledges the threat posed by malware. He advises a deep defence approach, modelled on the ISO27001 standards. Nath says future attacks could be targeted at virtual machines and cloud computing services, but conventional attacks would be common, as these are still more effective. He advises a holistic, multilayered, high-quality solution implementation by enterprises and government as a first line of defence.
Asked about the changing character of security solutions in light of the dynamic nature of threats, he says that the security industry is facing a complicated horizon – escalation in targeted attacks, increasing use of unsecured mobile devices at the workplace (or for work) and cloud implementations where data can be accessed anytime, anywhere.
With the proliferation of mobile devices or consumerisation of IT, coupled by virtualization or cloud adoption, Nath says the security needs to move closer to the application and data where it resides i.e. the host becomes self defending, be it mobile devices, virtual servers, or cloud servers. The strategy should be to ensure a higher degree of host defence by applying stronger & effective context aware security to protect the applications and data on the hosts.

Amit Nath
Country Manager, Trend Micro
“A holistic, multilayered, high-quality solution should be used by enterprises and government as a first line of defence”
Both Lobo and Nath point to increasing threat of malware on mobile devices. It is feared that roughly 300 million devices could be infected by mobile malware. Experts say that whereas mobile viruses may be effectively mitigated by antivirus products, mobile malware that gains access through downloads of malicious apps will be a difficult risk to manage.
Experts eGov spoke to are also optimistic about the positive impact that the impending adoption to IPV6 would have on security, but with caveats. As opposed to IPv4, IPv6 has been developed with security in mind, and as Nair points out, IPv6 eliminates some traditional network level attack vectors and provides mechanisms for maintaining transport confidentiality and integrity. Lobo sees the increased address space as a positive, saying the consequent reduction in sharing of IP addresses would make it easier to track down cyber criminals and cyber crime vectors like Botnets.
Jain points out that the IT infrastructure will have to ensure the IPv6 compatibility of firewalls, intrusion-prevention devices, and other security appliances to successfully deploy IPv6 avoiding possible security issues, and says it is at least 5 years to fully implement IPv6. Nair says that IPv6 might not essentially change things for the better as the major security issues have simply moved ‘up-the-stack’ to the application level in the new implementation.
Cyberterrorism – How big is the Threat?
Numerous movies have portrayed insanely smart, crooked programmers who get access to a nation’s vital defence systems to either launch nuclear weapons, or demand massive ransoms in return; or, worm their way into the financial system to either transfer billions to themselves or unleash a financial Armageddon. Just how real are such scenarios? What is cyberterrorism in the first place?
As with terrorism, cyberterrorism is a term that has defied a universal definition. However, in a testimony before the US House Armed Services Committee in May 2000, computer science professor Dorothy Denning identified some characteristic features of cyberterrorism:

Dr Kamlesh Bajaj
CEO, Data Security Council of India
“DSCI has developed DSCI Security Framework (DSF) for data security and DSCI Privacy Framework (DPF) for data privacy”
• Cyberterrorism is the convergence of cyberspace and terrorism
• It refers to unlawful attacks and threats of attacks against computers, networks and the information stored therein when done to intimidate or coerce a government or its people in furtherance of political or social objectives.
• A cyberterrorist attack would result in violence against persons or property, or at least cause enough harm to generate fear.
• Serious attacks against critical infrastructures could be acts of cyberterrorism, depending on their impact. Attacks that disrupt nonessential services or that are mainly a costly nuisance would not.
|
Anonymous— Templars or Rogues ? As its name suggests, Anonymous is an underground group with a very small core made up of The Anonymous signature line: We are Anonymous, We are Legion, We do not forgive, We do not forget, They should have expected us |
So how real is cyberterrorism?
Rammurthy says cyberterror is a big threat. He says Supervisory Control and Data Acquisition (SCADA) systems are favourite targets for cyber criminals as they have control over the critical infrastructures like government, large enterprises, etc. Echoing concerns about SCADA systems, Tech Mahindra’s Lobo says that although there have been no major incidents to date, inadequate security in SCADA systems can be targeted to cripple critical national infrastructure such as power, water, and nuclear facilities. There are plenty of opportunities to do so should these systems be connected or accessible via the Internet. SCADA systems the world over were not built for security and the cost for replacement or security refit is huge.
Noting that governments worldwide are prioritizing cyber security as both a national security and economic security issue, and have invested heavily in beefing up defences, RSA’s Shahani cites the growth in cyber crime, the rampant theft of IP and other sensitive information from corporations, and the penetration of defence systems and critical infrastructure by cyber attackers to emphasise upon the growing threats to cyber security. Shahani also says that the US Federal Government is ramping up its cyber security workforce plans and forecasts spending $13.3 billion on cyber security initiatives by 2015.
Jain chooses to focus more on the broader domain of cyber crimes. Saying user data is fast becoming the most valuable asset, he says increasing access to the Internet and gadgets such as laptops, smartphones and tablets means more and more people are carrying data on-the-go, and with the lack of proper security awareness among users, this data becomes a tempting target for cyber criminals. Data can be stolen through bots and the compromised system could be made part of a Botnet, or zombie network, consisting of thousands or even millions of compromised computers controlled from the botnet’s command and control centre. Botnets are used to steal bank data, emails, and perform such cyber attacks as spam, DDOS, phishing, click fraud, adware and malicious programs’ distribution.
Jain also says India is the world’s leading source of spam – In 2011 India continued to be on the top of the rank as about 15-17% of world’s spam traffic originated from India. Most of the spam is generated from compromised systems – In 2010 more than 700,000 IP addresses globally were infected with Rustock botnet and the majority of them were in India. This particular botnet was believed to send out as many as 40 billion spam emails per day. Distributed Denial of Service (DDoS) attacks through compromised ‘zombie’ systems are also of concern to experts we spoke to. DDoS has been widely deployed by hacker groups such as Anonymous (see box) to target large websites.
Industry Outlook
The future for security industry looks bright, given the rapidly evolving overall security scenario. It is, at the same time, also very challenging to keep up with the increasingly complex threats and explosion of platforms that we are witnessing. Jain sees spending on security by enterprise and SMB increasing at a good pace and sees major business potential from educational and government organisations.

Kutty Nair
Chairman & Managing Director, Mielesecurity
“The threats are growing daily, as evidenced by numerous breaches that have been uncovered. We should not be ostriches and pretend the problem does not exist”
Shahani prefers to focus on the technological trends when talking of industry outlook, and says the evolving computing paradigm presents vast opportunities for cyber criminals, hacktivist groups and nation states to exploit. We are facing a new reality – one of persistent, advanced and intelligent threat. In the wake of this phenomenon, CEOs and corporate boards are taking a keen, increased interest in security. In his view, shaken by the wave of attacks in 2011, corporations would endeavour to make 2012 an year of action towards ensuring better security of their information assets.
Rammurthy concurs with the rosy predictions for revenue, quoting Gartner estimates of the security software market in India touching US$ 209 million in 2011 and is forecasted to grow to US$ 320 million in 2014.
Privacy Issues
The debate over privacy has been getting increasingly heated in India of late. Particularly since the IT Rules (under the 2008 Amendment), were notified in April 2011 privacy advocates are up in arms. However, the government has been citing national security concerns, and the need for maintaining public order as the two main motives driving its actions. Privacy and web-censorship related issues got a fresh lease of life when last month, representatives of social media giants such as Google, Facebook and Twitter etc were summoned by the government and asked to devise mechanisms for screening of potentially objectionable content. 21 companies are currently embroiled in a case alleging they have violated Indian laws related to what kind of information can be published in the public domain, and have also been blamed with endangering national security under various sections of the Indian Penal Code. The outcome of this case will be keenly watched across the globe.
Defending the government’s stance, CERTIn DG Gulshan Rai says the government is one of the stakeholders in this entire debate, and is committed to protecting privacy and freedom of expression. In his view, there is a delicate balance among three concerns – privacy, national security and the right to information, and the government is trying to find an equilibrium. Rai also says that the provisions on data safety and security incorporated in the IT Act are ahead of similar provisions elsewhere, and that the recently unveiled Data Protection Policy of the EU borrows several ideas from the Indian Act.
Pankaj Jain is of the view that the Indian law enforcement agencies are at the very initial stage of developing policies and practices in cyber privacy surveillance, and seconds Rai’s opinion regarding the need for a balance between the need for security and privacy.
Saying that individuals need to raise their awareness on data privacy and on their rights available under Indian laws, Rahul Jain, Senior Consultant with the DSCI, advocates constant vigilance when providing personal data to third parties. He points out that quite often, we freely disclose personal details without even knowing the purpose for which it is collected and ascertaining if the other party is collecting information more than what is required. He also stresses upon the need for keeping oneself aware of the latest developments related to cyber crime and following basic security practices such as checking authenticity of sites, not saving & sharing passwords, installing suspicious software & applications, etc.
The increase in surveillance and monitoring by security agencies vs. privacy is an ongoing debate. To an extent, monitoring and surveillance does impact privacy, however, appropriate balance between both is the only way out.
Reflecting the general consensus, Lobo also admits that the issue of privacy and free speech vs. national security is a complicated one with few easy answers. As others, he also advocates clarity in laws and procedures that allow government to snoop upon private information, and to censor speech on the web.
|
Wikileaks – Information Warrior or Sensationalist? WikiLeaks, a non-profit that says its goal is to bring important news and information to the public, had been in the business of leaking confidential government and corporate information for a while. November 2011 was different, however. In this month, WikiLeaks commenced sequential release of over 2,50,000 secret US diplomatic cables that had been stolen by Bradley Manning – a US military analyst now under incarceration.
Following the massive leak, WikiLeaks came under sustained fire from a number of governments. It has also sparked a yet-inconclusive debate on the correctness of its actions and the impact these would have on international relations. WikiLeaks has also triggered a massive review of information security protocols in a number of countries and it is unlikely that another Manning could leak classified information as easily as by copying it onto a Lady Gaga CD. |
WRITE BACK
Your views and feedback matter to us. Tell us what you think of the stories in the magazine or what more you would like us to cover. Write back to us at editor@elets.in
Be a part of Elets Collaborative Initiatives. Join Us for Upcoming Events and explore business opportunities. Like us on Facebook , connect with us on LinkedIn and follow us on Twitter, Instagram.


 expert hackers. Anonymous has made quite a splash for itself in the virtual world, targeting leading sites such as PayPal, Mastercard, Visa and Amazon, Bank of America, The United States Department of Defense, The United Nations, and Lockheed Martin etc. Anonymous has also brought down sites in support of the Iranian protests and also the Arab Spring uprisings. Its most recent victims include CBS and Universal Music, in response to their backing of the (stillborn) controversial anti-piracy legislations SOPA and PIPA . Anonymous have also (repeatedly) hacked into the Sony Playstation network, and recently put out a warning to Sony, telling its support for SOPA would invite another attack, and asked it to be “prepared to be extinguished”. Sony and Nintendo withdrew support to SOPA following threats by Anonymous. Anonymous have written a software – Low Orbit Ion Cannon (LOIC) – that launches a coordinated Distributed Denial of Service (DDoS) attack on target websites, overwhelming the servers with hundreds of thousands of data packets and crashing them. Anonymous had also targeted one of the world’s largest websites – Facebook, running on over 60,000 servers – for a takedown on January 28. This was the most audacious attack ever announced by the group but they were not successful in bringing Facebook down.
expert hackers. Anonymous has made quite a splash for itself in the virtual world, targeting leading sites such as PayPal, Mastercard, Visa and Amazon, Bank of America, The United States Department of Defense, The United Nations, and Lockheed Martin etc. Anonymous has also brought down sites in support of the Iranian protests and also the Arab Spring uprisings. Its most recent victims include CBS and Universal Music, in response to their backing of the (stillborn) controversial anti-piracy legislations SOPA and PIPA . Anonymous have also (repeatedly) hacked into the Sony Playstation network, and recently put out a warning to Sony, telling its support for SOPA would invite another attack, and asked it to be “prepared to be extinguished”. Sony and Nintendo withdrew support to SOPA following threats by Anonymous. Anonymous have written a software – Low Orbit Ion Cannon (LOIC) – that launches a coordinated Distributed Denial of Service (DDoS) attack on target websites, overwhelming the servers with hundreds of thousands of data packets and crashing them. Anonymous had also targeted one of the world’s largest websites – Facebook, running on over 60,000 servers – for a takedown on January 28. This was the most audacious attack ever announced by the group but they were not successful in bringing Facebook down.








