Growing use of Information Technology today calls for ensuring greater security of data in all its forms, writes Sunil Kumar, Elets News Network (ENN)
Information technology has grown significantly over the years, and so has the concern for information security for businesses, consumers and governments alike. With the ever-rising use of Internet, the issue of security is also getting complex by the day. Adoption of smart devices by employees also calls for greater security measures at companies.
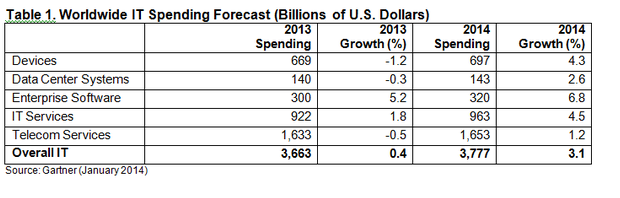
IT threats are becoming more sophisticated all over the world and organisations are demanding new, robust, affordable and upgraded security solutions in order to protect their confidential data. Security for the IT sector is no longer a choice; it is a core part of any solution implementation. Therefore, both government and private organisations are spending generously on it: of an average IT spend of 11-15 percent, 2-3 percent goes toward security.

Dr Shefali Dash, Director General, National Informatics Centre (NIC)
“A trusted and resilient digital infrastructure that can withstand attacks would provide a platform for innovation and prosperity, the benefits of which could be reaped by the common man at the grass root level”

According to a joint study conducted the IDC and the National University of Singapore (NUS), enterprises would soon be spending $127 billion on security issues and $364 billion dealing with data breaches.
 There has been a considerable change in the way IT services are being used by enterprises. For instance, security solutions such as antivirus and firewalls cannot guarantee a network system against data theft or cyber crime. This has led to changes in the demand for security solutions. The rise in the usage of virtualisation and cloud computing has made network gateways redundant. While it’s been common for enterprises to use the Internet for business-to-business and business-to-consumer transactions, the governments are also beginning to do that. Also, the use of social software within organisations is on the rise, which will further raise security threats. In such a scenario, safeguarding an organisation’s data assumes utmost importance.
There has been a considerable change in the way IT services are being used by enterprises. For instance, security solutions such as antivirus and firewalls cannot guarantee a network system against data theft or cyber crime. This has led to changes in the demand for security solutions. The rise in the usage of virtualisation and cloud computing has made network gateways redundant. While it’s been common for enterprises to use the Internet for business-to-business and business-to-consumer transactions, the governments are also beginning to do that. Also, the use of social software within organisations is on the rise, which will further raise security threats. In such a scenario, safeguarding an organisation’s data assumes utmost importance.
Security and Governance
Security challenges for governments are much bigger and broader. With the government making its operations computerised and centralised, challenges of securing data has become further difficult. Since all applications used in e-governance are web based and open to public, they are prone to attacks. Data Centre Security solutions have to be deployed at every stage of the network.
Abhishek Singh, Executive Director (IT), Food Corporation of India
“The data security and importance of Information and IT security is very critical for people in the government. But the way technology is growing and the way ICT, Internet and web-enabled technologies are dominating our lives, it is important for us to ensure that we have safe and secure data”
Rajesh Maurya, Country Manager, India & SAARC, Fortinet
“The era of e-Governance has not only improved public services it has also made the access to services simple and fast. Because of this transition from traditional to web based Governance, the risk of sensitive public information being stolen or compromised has increased dramatically.”
When it comes to the government sector, cyber security becomes a matter of national security. The current approach of the government is quite systematic and they are taking serious and measured steps towards ensuring their data protection strategy. The government is spending significant money on securing their infrastructure.Using integrated security solutions such as Unified Threat Management (UTM) or next generation firewalls, government establishments can strengthen security defences and also experience a visible improvement in bandwidth utilisation and network performance.
Sunil Sharma, VP Sales & Operations – India & SAARC, Cyberoam
“Security devices deployed at many places lack proper configuration and integration with other systems. There’s a need to address this situation; government and PSUs require overhauling their networks, security appliances and security practices”
Securing the Network
Network security is a highly evolved technology that brings plenty of powerful tools and technologies to provide networks the safety cover. The Indian network security market is experiencing very high growth rate compared to other markets. According to market analysts, enterprise security market in India is expected to touch $548.7 million (about Rs 3,400 crore) this very year, logging a growth rate of over 14 per cent. The wireless network security market is projected to grow from $8.47 billion in 2014 to $15.55 billion by 2019, at a compound annual growth rate (CAGR) of 12.94 percent during the forecast period, according to a report ‘Wireless Network Security Market by Solutions, Services Worldwide Market Forecasts and Analysis (2014-2019)’.
Rajesh Maurya, Country Manager, India & SAARC, Fortinet said “The Indian network security market was pegged at US$ 233.2 million with a 2.2% YOY growth in 2013 according to Frost & Sullivan. The Government vertical registered a very small growth rate of 0.7% YOY in 2013.”
Sunil Sharma, VP Sales & Operations – India & SAARC, Cyberoam said “Today network security is not only about securing but has to address performance and compliance needs as well business networks. As more SMBs and SMEs adopt integrated security solutions such as Unified Threat Management, it is adding to growing demand for network security. The same is adding to our advantage given our spread and robust reach into these segments.”
Technologies on hand
With the advent of more and more technologies, even customised solutions are available to meet the requirements of every individual organisation. Of late, companies globally have started dumping standalone security tools like firewalls, VPNs, gateways etc. in favour of integrated platforms for cost efficiency and manageability.
RFID: RFID technology is the wireless non-contact use of radio-frequency electromagnetic fields to transfer data for the purposes of automatically identifying and tracking tags attached to objects. RFID can be used in tracking shipping containers, railroads, supply chain, mining, postal, livestock, toll collection and airline applications etc. From security point of view, RFID can be used for ports and border control. RFID-based weapons tracking solutions secure armaments for military, law enforcement and other agencies. According to a report –India RFID Market Forecast & Opportunities, 2018 – from Reportlinker, the RFID market in India is forecasted to grow at the CAGR of around 25 percent during 2013-2018.
According to IDTechEx, in 2014, the total RFID market is worth $9.2 billion, up from $7.88 billion in 2013 and $6.98 billion in 2012.
Smart Cards: Smart cards are credit card-sized plastic cards with an embedded computer chip. The chip can either be a microprocessor with internal memory or a memory chip with non-programmable logic, connectable via direct physical contact or remotely via a contact less electromagnetic interface. Those cards can provide identification, authentication, data storage and application processing. Smart cards may provide strong security authentication for single sign-on (SSO) within large organisations. Today smart card technologies are used in various areas, like healthcare, banking, entertainment and transportation.
Smart cards can serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorisation cards for pay television, household utility pre-payment cards, high-security identification and access-control cards, and public transport and public phone payment cards. Smart cards offer various benefits such as quick transactions, inbuilt security and portability, and can be used for identification, validation and data storage.
Cyber Security
With the era of website defacement gradually making room for theft of sensitive information, cyber security attacks are the order of the day. Cyber attackers these days try to make holes in the defence and security systems of a country. A significant increase in cyber space activities in the country has resulted in increased opportunities for technology-related crime. Besides, lack of user-end discipline, inadequate protection of computer systems and the possibility of anonymous use of ICT – allowing users to impersonate and cover their tracks of crime – have encouraged a growing number of users to experiment with ICT abuse.
The Government of India had set up an Inter-Departmental Information Security Task Force (ISTF) with the National Security Council as the nodal agency to monitor the increasing incidences of cyber crime. Acting on the task force’s recommendations, the following initiatives have been taken:
• Indian Computer Emergency Response Team (CERT-In) has been formed to respond to the cyber security incidents;
• Public key infrastructure (PKI) has been put in place to support implementation of the Information Technology Act and promote use of digital signatures; and
• Initiatives undertaken to support anti-cyber crime R&D activities through premier academic and public sector institutions in the country.
The government has mandated implementation of security policy in accordance with the information security management standard ISO 27001.
Dr Gulshan Rai, Director General, CERT-IN
“We are living in an era when things are much different in terms of technology, process and technique. From mere hacking to cyber espionage to attacks from faux servers – the nature of cyber space attacks has evolved over the years. This is time of cyber warfare…we must deal with it effectively”
 Satya Narayan Pradhan, Additional DG, CID, Jharkhand
Satya Narayan Pradhan, Additional DG, CID, Jharkhand
“All police and security organisations of the Government, whether at the Centre or the State level must seriously look into issues like their cyber infrastructure security and data security. We must not forget that much if not all of Governance in the foreseeable future is going to be data driven. CCTNS and other allied projects will necessarily mean a policing infrastructure and process that will rely much on digital data. It is high time therefore that we learn how to secure it and the infrastructure on which it sits and operates. The sooner it is planned and implemented the better”
The IT infrastructure has become an integral part of the critical infrastructure like power grids, emergency communication systems, financial systems, defence systems and air traffic control networks. The operational stability and security of information infrastructure is vital for economic security of the country. As the cyber space has room for both vitiating the environment and, if used correctly, to deliver in a positive manner, let us give the second option a try.
Be a part of Elets Collaborative Initiatives. Join Us for Upcoming Events and explore business opportunities. Like us on Facebook , connect with us on LinkedIn and follow us on Twitter, Instagram.