A structured approach towards addressing information management challenges is immediately needed
 By Arvind Mehrotra,
By Arvind Mehrotra,
President APAC, NIIT Technologies
The principle of PDCA (Plan, Do, Check and Act) is an important paradigm In information management and security. Although a lot of work has gone in planning and evolving policy structures for egovernance, implementation can only be as successful as the strength of the monitoring mechanism. We thus need to strengthen our monitoring abilities to manage information and ensure security of data in a more robust and effective manner
.
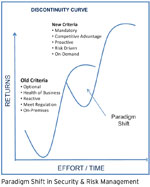 Challenge for Indian security environment is largely coming from the threat of loss of reputation that arises from attack on websites that are your public face. About 270 Indian official sites have been hacked in recent times. So far, we have not really tried to undertake forensic analysis of the incidents and close the loopholes. With the changing forms of attacks, we need to be proactive and deal with policy and administrative aspects appropriately so that the security of our information assets is not compromised.
Challenge for Indian security environment is largely coming from the threat of loss of reputation that arises from attack on websites that are your public face. About 270 Indian official sites have been hacked in recent times. So far, we have not really tried to undertake forensic analysis of the incidents and close the loopholes. With the changing forms of attacks, we need to be proactive and deal with policy and administrative aspects appropriately so that the security of our information assets is not compromised.

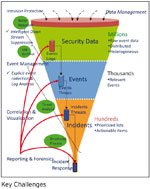
Key Challenges

There are four sets of challenges that we need to address in order to put in place an effective information management system.

Managing datasets is the first challenge. We need to manage different datasets that need to be integrated. The present egovernance model talks of more and more public facing systems that can increase transparency and reduce costs besides creating trust among the people. In order to ensure reliable service delivery, there is a critical need to manage data, guard against unauthorised intrusions and create audit trails that can help in forensic analysis of any untoward event.
 The next challenge is a macro-level view of risk management in governance. While the RBI has mandated corporates to adopt risk management and corporate governance norms under Clause 49, the risk management framework in governments is still weak. I am yet to come across any govt in India that has adopted an ISMS (Integrated Security Management Policy) policy. This needs to be addressed on a priority basis.
The next challenge is a macro-level view of risk management in governance. While the RBI has mandated corporates to adopt risk management and corporate governance norms under Clause 49, the risk management framework in governments is still weak. I am yet to come across any govt in India that has adopted an ISMS (Integrated Security Management Policy) policy. This needs to be addressed on a priority basis.
The third challenge is that as we adopt ICT in governance, we are increasingly deploying multiple sets of technology without knowing exact roles of each set. Consequently, there might be multiple systems performing the same function. In the absence of a data analysis engine that can collate and analyse data across systems, and manage the dataset, this might go undetected. In addition, in the absence of a centralised analytics system, the information being generated from diverse deployments often goes unutilised. This too needs to be addressed.
Lastly, we also need to address the absence of proper controls and an assessment and risk mitigation strategy. At present, there is no process that can judge the performance of a technology deployment against pre-defined performance criteria and against its adherence to policy guidelines. There is similarly no proper framework to analyse whether or not the technology is able to adequately protect the data assets. All this needs to change.
The earlier model of governance working in unconnected silos is being replaced by a new paradigm of interconnected applications and integrated datasets. We now need a process view that addresses all issues in an integrated manner. A Security Operating Centre dealing with security incident management services and adoption of the CTO/CIO model in governments for better management of our information assets need to be adopted with urgency.
Be a part of Elets Collaborative Initiatives. Join Us for Upcoming Events and explore business opportunities. Like us on Facebook , connect with us on LinkedIn and follow us on Twitter, Instagram.
"Exciting news! Elets technomedia is now on WhatsApp Channels Subscribe today by clicking the link and stay updated with the latest insights!" Click here!