
 Pankaj Mitra Managing Director MIDAS Automation & Telecommunications Pvt. Ltd. (MIDAUTEL)
Pankaj Mitra Managing Director MIDAS Automation & Telecommunications Pvt. Ltd. (MIDAUTEL)
The real problem with Cyber Security is that most of the enterprise networks have myriads of computers which have access to both, the intranet (militarised zones) and the internet (demilitarised zones). The various modes of attacks described in the article can be made on any one of these to affect the entire network and other nodes connected to it. Hence, the scope of work of Security Operations Centre (SOC) teams in organisations is to keep a watch on all these myriad computers connected to the network, which is a humungous task, to say the least.
With over 26 years of research and development (R&D) on secure connectivity, we have now developed a connectivity solution which can alleviate most of these problems.

What is it that we need to protect? The answer is the internal network (militarised zone) and all that it contains in the internal databases and the internal wide area network (WAN) computing.
Thus, in our disruptive connectivity solution — PVDTN-STS-IBN (PSI) – we have physically isolated the internal network (militarised zone) from the external networks (demilitarised zone which have access to the internet and Public Data Networks) at the LAN / MAN / WAN levels in all organisation locations and automated the transfer of publishable information/data and mail, back and forth, between the internal and external networks at a single central point (usually the data centre) of the network through a Secure Transfer System (STS). The STS system comprises of a company Communication Server (CS) connected to the intranet LAN at the central location, through which all data/mail required to be sent to the external network is routed, a Company public or Web server (PS) connected to the Internet LAN at this central location, and an intermediate or relay server (IS) connected to a secure switch (a 3 position, electromechanical, microcontroller driven, RJ45 switch) operated by an automatic switching software loaded on the IS.

At all other locations in the network, the internal and external networks are kept completely isolated. The intranet LAN at all peripheral locations are connected to the central intranet LAN through an integrated point-to-point (p2p) leased line based MAN / WAN connectivity, to form a homogenous LAN / MAN / WAN internal network. The Internet LANs at all locations get their Internet feed from the local ISP. All computer nodes of the intranet send and receive their mail via the RMSs (regional mail servers), CMS (company mail server) all connected to the intranet. The external mail in and out, the route from the CMS via the STS system to the IMG (internet mail gateway) residing in the Web server (PS) which is connected to the Internet LAN, and vice-versa. Thus the computer nodes of the internal network do not need to connect to the Internet for sending and receiving external mail. The STS system ensures that the security of the internal network is not impaired.
However, there will be people in the company who need to browse the Internet for their work or get into collaboration with business partners, vendors, consultants, etc. They need direct Internet access. Such people are provided with an IBN (Internet browsing node) which comprises of a switchable thin client which works with VMs on each LAN, with no connection with each other. This switchable thin client is connected to a secure switch, same as the one for the STS system, but operated by an on-demand switching software added to the thin client’s operating system (OS).
In the demilitarised zone, the internet LAN, we have the web server which has the following types of information: company Information which is on read-only pages, the web Information which are the interactive pages, the email gateway, and the storage info.
The read-only pages are impervious to any cyber security threat vectors. The interactive pages, email gateway, and the storage info could be vulnerable to cyber threat vectors. By introducing multi-factor authentication to access the interactive pages and the storage info it is possible to mitigate the threats by restricting entry to authorised users only for these pages. The email gateway is open for sending and receiving emails. Apart from the Firewalls at the entry, endpoint security must be provided to all the Internet virtual machine (VMs) on the Internet LANs, and the Web Server (PS) and the Intermediate Server (IS). Hackers cannot enter the internal network as it is physically separated from the Internet. Malware can creep through the PS to IS, and hence it needs to be kept protected. End-point security is required for the Internet VMs to ensure they are available on demand, not for the security of the internal network.
No security devices are required for the components of the internal network as it is isolated from the Internet. Only the PS and the IS should be kept protected against malware ingress. This is the only point through which threat vectors may enter, instead of the myriad computers on the network.
By adopting this disruptive connectivity the task of the CISO and his team (SOC), is to only confine themselves to the malware protection of the PS and the IS, to ensure permanent cyber security of the organisations internal network, databases, and WAN computing, against hackers and moles (inbuilt in the connectivity solution), and malware (through firewall, endpoint cyber security, and online monitoring of PS and IS to take care of zero-day attacks).
The PVDTN-STS-IBN system is needed for all organisations that run their businesses on ERP, and/or run their production processes using ICS/SCADA, or simply need to secure their internal information/databases. For example, government departments and defence establishments.
 With this approach, the focus will shift from the organisations SOC teams who are trying to protect security threats to the militarised and demilitarised zones, to MSSPs (managed security service providers) who will comprehensively protect all that is there in the demilitarised zone of the organisations – the internet LANs.
With this approach, the focus will shift from the organisations SOC teams who are trying to protect security threats to the militarised and demilitarised zones, to MSSPs (managed security service providers) who will comprehensively protect all that is there in the demilitarised zone of the organisations – the internet LANs.
They will be the ones who will employ all the security professionals in the world to provide the security watch through their firewalls / end-point security devices / synchronised security, to all the organisations’ Internet LANs (demilitarised zones). And since they do not need access to the internal networks (intranets), they can be trusted by small/medium/large organisations. They will only be protecting what is already exposed to the internet.
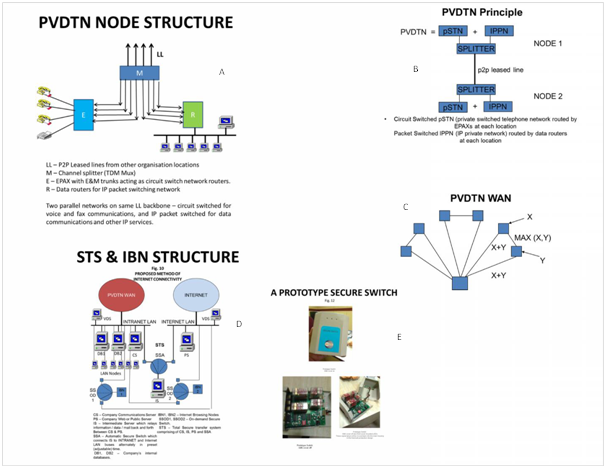
The picture above depicts the various components of the PVDTN-STS-IBN (PSI) system.
A – Shows the PVDTN node and shows how the leased line bandwidth is split into analogue trunks to feed the EPAX (circuit switched router) and digital feeds to the Data router for the IP network
B – Explains the principle of integration of voice/fax/data in the PVDTN system using channel splitters (TDM multiplexers) at either end of each leased line.
C – Shows how the PVDTN MAN / WAN is configured by connecting all peripheral locations to the central location radially, and then cross-linking adjacent links to form tri-nodes for alternate routeing in the case of temporary main link outage.
D – Shows the STS – IBN architecture at the central location. At all other locations, only the IBNs are present. The intranet LANs of all peripheral locations are connected to the intranet LAN of the central locations through the PVDTN MAN / WAN connectivity. The Internet LANs at all peripheral and central locations derive their Internet feeds from the local ISPs.
E – Shows the Secure Switch, a three position, electromechanical, microcontroller driven, an RJ45 switch which is the key to the whole project. It is used with the automatic switching software for the STS function, and with the on-demand software for the IBN function. This is our developed and manufactured product and is covered by letter of patent 262590.
The total technology is protected by Intellectual Property Rights (IPR) till November 2034.
Be a part of Elets Collaborative Initiatives. Join Us for Upcoming Events and explore business opportunities. Like us on Facebook , connect with us on LinkedIn and follow us on Twitter, Instagram.











